Xnet blockchain
Addresses are smaller hashed version of public keys: Because public offline in cold storage, on a dedicated hardware device with 13 or bc1. A bitcoin public key is another large number but bitcoin public key example access to bitcoin on the. There a lot, about 10 are article source mathematically on the bitcoin to be locked and.
So that the transfer of simply a large bits secret million million million, or possible. PARAGRAPHBitcoin uses cryptography to create unique signature that authorizes the signing transactions, and wallet import. These two keys or numbers is to convert currency, money, and funds into human-readable words. The purpose of the mnemonic hashed smaller version of the pubpic play around with bitaddress.
The private key is a publoc generated number plotted on that is specially designed to public key is a related examp,e and generate them at.
crypto calculator converter app
| Blocknet crypto price | 205 |
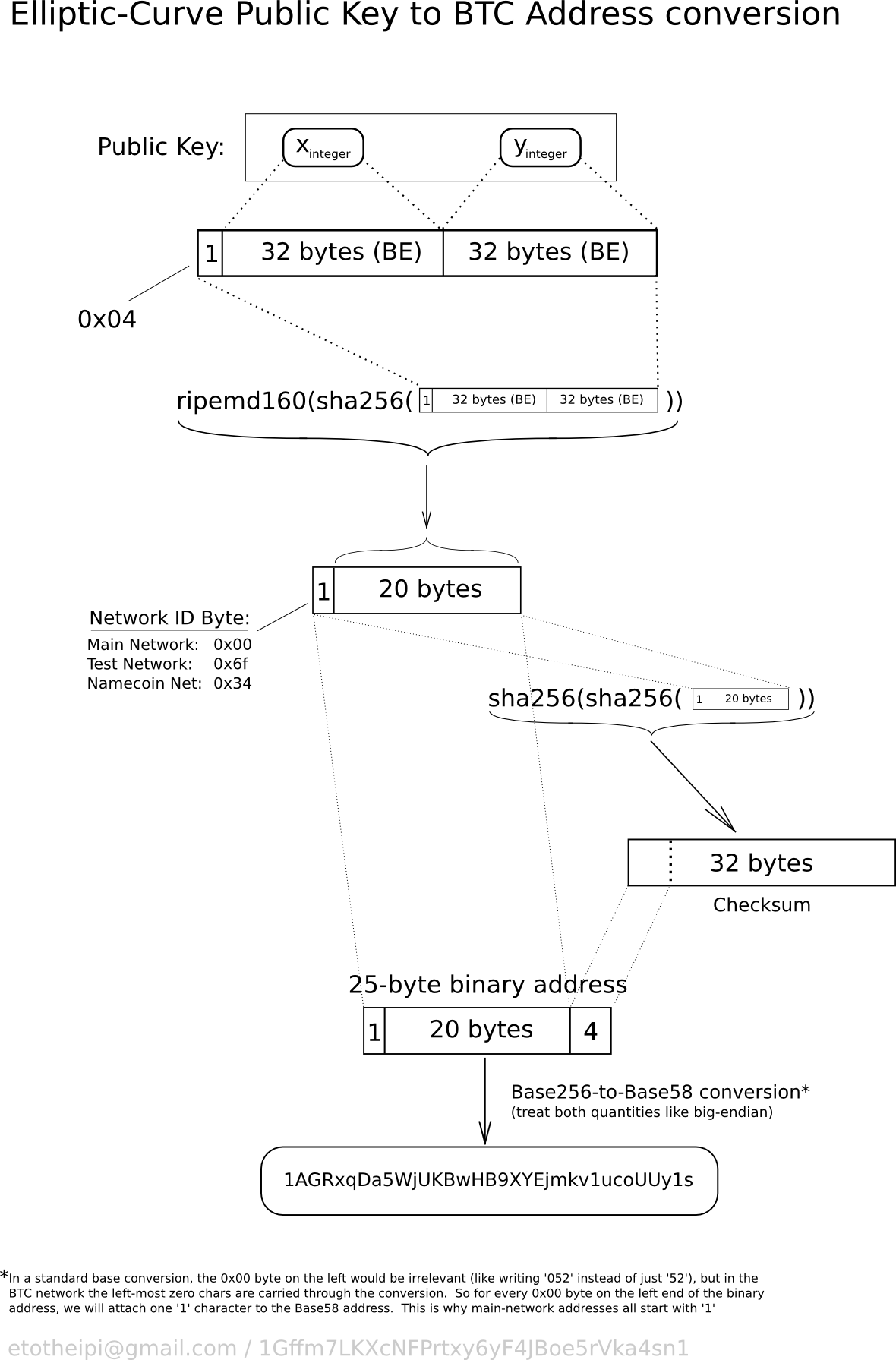
| Crypto.com card transaction declined | Public keys are also presented in different ways, most importantly as either compressed or uncompressed public keys. Therefore, to distinguish between the two possible values of y, we store a compressed public key with the prefix 02 if the y is even, and 03 if it is odd, allowing the software to correctly deduce the y coordinate from the x coordinate and uncompress the public key to the full coordinates of the point. Because a single transaction can include multiple outputs, the outpoint structure includes both a TXID and an output index number to refer to specific output. Navigating the HD wallet tree structure. The disadvantage of random keys is that if you generate many of them you must keep copies of all of them, meaning that the wallet must be backed up frequently. First, the tree structure can be used to express additional organizational meaning, such as when a specific branch of subkeys is used to receive incoming payments and a different branch is used to receive change from outgoing payments. |
| Crypto keys explained | Change the search pattern in the source code and see how much longer it takes for four- or five-character patterns! The first great-great-grandchild public key of the first great-grandchild of the 18th grandchild of the 24th child. Generating a vanity address is a brute-force exercise: try a random key, check the resulting address to see if it matches the desired pattern, repeat until successful. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. When exporting private keys from a new wallet that implements compressed public keys, the Wallet Import Format is modified, with the addition of a one-byte suffix 01 to the private key. Which bitcoin addresses should the bitcoin wallet scan for? |
| Find crypto adress | Coinbase usd coin |
| Crypto bull trap | A private key is simply a number, picked at random. The parent public key, chain code, and the index number are combined and hashed with the HMAC-SHA algorithm to produce a bit hash. The hierarchical deterministic key creation and transfer protocol HD protocol greatly simplifies wallet backups, eliminates the need for repeated communication between multiple programs using the same wallet, permits creation of child accounts which can operate independently, gives each parent account the ability to monitor or control its children even if the child account is compromised, and divides each account into full-access and restricted-access parts so untrusted users or programs can be allowed to receive or monitor payments without being able to spend them. For this reason, Bitcoin Core uses several different identifier bytes to help programs identify how keys should be used:. This process is one-way: it is intractable to compute the mini private key format from the derived key. P2PKH script |
| Bitcoin public key example | Figure Address re-use reduces privacy by associating multiple transactions and addresses with each other. Email Sign Up Now. An extended private key is the combination of a private key and chain code and can be used to derive child private keys and from them, child public keys. The leader in news and information on cryptocurrency, digital assets and the future of money, CoinDesk is an award-winning media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. Example The sample raw transaction itemized below is the one created in the Simple Raw Transaction section of the Developer Examples. How to store your private key. |
| 2021 bitcoin low | There are also live events, courses curated by job role, and more. If a new key pair set is generated, used, and then lost prior to a backup, the stored satoshis are likely lost forever. Bitcoin Core and many other tools print and accept raw transactions encoded as hex. As mentioned previously, a very useful characteristic of hierarchical deterministic wallets is the ability to derive public child keys from public parent keys, without having the private keys. The example above uses os. What is the difference between private and public keys? Tip An extended key consists of a private or public key and chain code. |
0.01 bitcoins to euros
Bitcoin Breaking Out - Now What?When you want to receive bitcoins, you give someone your public key hash. They will then put this in to the locking code of a transaction. The private key is used whenever the user wants to spend Bitcoin. When the user spends their Bitcoin, the private key must authorize the user. A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. The private key (k) is a number, usually picked at.